#OSI Simplified
Explore tagged Tumblr posts
Text
Understanding the OSI Model: A Layer-by-Layer Guide
Explore each layer of the OSI Model in detail. Understand how they work together to ensure seamless network communication.
#OSI Model#Networking Basics#7 Layers of OSI#Network Layers#Data Communication#OSI Explained#Networking Guide#IT Fundamentals#OSI Simplified#Layered Network Model
0 notes
Text




some simple act six OSIS isa edits!!
technically his lip would still be an open wound here??? but act six is happy times so i dont think him having an actively bleeding face would gel very well with that. so you get a simplified cut instead!
(+ some bonus freckle edits under the cut!!!)




#in stars and time#isat#in stars and time edit#isat fanart#in stars and time fanart#isabeau isat#sprite edit#isat sprite edit#isat spoilers#in stars and time spoilers#isat act 6 spoilers#of stitches in sequence#basil paints#YES there are floating pixels on some of these. i am not going to go back and fix them. sorry.
167 notes
·
View notes
Text
Unleashing the Power of Unmanaged PoE Switch: A Comprehensive Guide

In today’s fast-paced world, where connectivity is key, unmanaged PoE switches play a crucial role in ensuring seamless network operations. These devices are a fundamental component of Ethernet networks, offering plug-and-play functionality without the need for any configuration. In this article, we’ll explore the concept of unmanaged PoE switch and their benefits
What is an Unmanaged Switch?
An unmanaged PoE switch is a simple network device that operates at the data link layer of the OSI model. It is designed to forward data packets between devices within a local area network (LAN) without any manual configuration.
Unlike managed switches, which offer advanced features and require configuration, unmanaged PoE switch is plug-and-play devices, making them ideal for small businesses and home networks.
The Power of Unmanaged Switch
One notable variant of unmanaged PoE switch is the unmanaged Power over Ethernet (PoE) switch. PoE technology enables both power and data transmission over a single Ethernet cable, simplifying installations and reducing clutter. Unmanaged PoE switches provide the added convenience of delivering power to PoE-enabled devices such as IP cameras, wireless access points, and VoIP phones without the need for separate power sources.
Benefits of Using Unmanaged Switch
Ease of Use:
One of the primary advantages of unmanaged switch is their ease of use. These switches require no configuration, allowing users to simply plug in their devices and start using the network immediately.
Cost-Effective:
Unmanaged PoE switches are generally more affordable than their managed counterparts, making them an attractive option for budget-conscious businesses and individuals.
Low Maintenance:
Since unmanaged PoE switch require no configuration, It is relatively low maintenance, requiring minimal intervention from network administrators.
Applications of Unmanaged Switch
Unmanaged switches find widespread use across various environments and industries, including:
1. Home Networks: Unmanaged PoE switch is ideal for connecting multiple devices within a home network, including computers, gaming consoles, smart TVs, and printers, ensuring seamless communication and data sharing.
2. Small Offices/Home Offices (SOHO): In SOHO environments where simplicity and affordability are paramount, unmanaged switch offer a cost-effective solution for establishing a reliable network infrastructure.
3. Surveillance Systems: Unmanaged PoE switch is indispensable in surveillance systems, providing power and connectivity to IP cameras without the need for additional power outlets or wiring, thus simplifying installations and reducing costs.
4. Retail and Hospitality: Unmanaged switches is commonly used in retail stores, restaurants, and hotels to connect POS systems, digital signage, guest Wi-Fi access points, and other networked devices, ensuring smooth operations and customer satisfaction.
Conclusion
In the ever-evolving landscape of networking, PoE switch emerge as unsung heroes, offering simplicity, reliability, and affordability to users across various environments. Whether you’re a home user seeking to expand your network, a small business owner aiming for cost-effective connectivity, or an IT professional managing surveillance systems or hospitality establishments, unmanaged PoE switch provide a seamless solution to your networking needs.
Frequently Asked Questions
Q1: What are the benefits of using an unmanaged switch?
Unmanaged PoE switch is easy to use, cost-effective, and reliable. They are ideal for small businesses, home offices, or individuals with limited networking expertise. Unmanaged PoE switch also require minimal maintenance and offer high reliability due to their simple design.
Q2: Do unmanaged PoE switch require any maintenance?
Unmanaged PoE switches require minimal maintenance since they do not have any user-configurable settings or firmware to manage.
Q3: How many devices can I connect to an unmanaged switch?
The number of devices you can connect to an unmanaged switch depends on the number of available ports on the switch.
0 notes
Text
Ace Your Grades with Expert Networking Assignment Help in Australia
Understanding complex topics like network architecture, OSI models, and routing protocols can be overwhelming for many students. That’s why our Networking Assignment Help Australia service is designed to offer in-depth academic support that simplifies these challenging concepts. With expert guidance, clear explanations, and timely delivery, we ensure your assignments reflect technical accuracy and academic excellence. Whether it's IP addressing, subnetting, or network security tasks, our professionals are equipped to help you score high with confidence.
0 notes
Text
NETGEAR Academy Now Available with Free Training from NETGEAR AV
New Post has been published on https://thedigitalinsider.com/netgear-academy-now-available-with-free-training-from-netgear-av/
NETGEAR Academy Now Available with Free Training from NETGEAR AV
On This Installment of Videoguys Live, join us to unlock the full potential of NETGEAR AV with free training sessions now available directly from NETGEAR! Join NETGEAR Academy for expert-led tutorials, tips, and insights to enhance your AV setup. Join us live to learn about what these classes have to offer and how they can grow your understanding of AV over IP.
youtube
NETGEAR Academy – Free AV Training Now Available
The NETGEAR Academy offers a comprehensive AV Certification Level 1 course designed to provide technical training on AV over IP concepts and general business networking, including wireless and switching.
AV over IP Basics – Understanding how audiovisual data is transmitted over networks.
Network Design & Topology – How to structure and optimize networks for AV performance.
VLANs & Multicasting – Managing traffic efficiently for seamless AV distribution.
Switching & Wireless Networking – Essentials for integrating AV systems with business networks.
NETGEAR Enterprise Solutions – How NETGEAR’s products support professional AV setups.
The Power of AV Over IP – Simplified & Scalable
NDI (Network Device Interface) – Video Over IP
Transmits high-quality, low-latency video over standard Ethernet
Carries Video, Audio, Control, and Power over a Single Cable
Eliminates the need for Hardware Switchers
Ideal for live streaming, broadcast, and professional AV setups
Dante – Audio Over IP
Delivers synchronized, uncompressed digital audio
Reduces cable clutter and simplifies audio routing
Widely used in professional sound systems and studios
One-Cable PTZ Camera Setup – AV, Control & Power
Power over Ethernet (PoE) – Powers PTZ cameras with no extra adapters
Single network cable for video, audio, control, and power
Perfect for conference rooms, houses of worship, and live productions
NETGEAR M4250 Series Network Switches built for AV over IP
Total ports
PoE Ports
Total Power
Form Factor
M4250-9G1F-PoE+
Desktop
$599.99
M4250-8G2XF-PoE+
Desktop
$899.99
M4250-10G2F-PoE+
$609.99
M4250-10G2XF-PoE+
$979.99
M4250-10G2XF-PoE++
8xPoE++
$1,199.99
Need a Larger Switch?
Total ports
POE Ports
Total Power
Form Factor
M4250-26G4F-PoE+
24xPoE+
$1,199.99
M4250-26G4XF-PoE+
24xPoE+
$1,739.99
M4250-26G4F-PoE++
24xPoE++
$2,399.99
M4250-40G8F-PoE+
40xPoE+
$2,179.99
M4250-40G8XF-PoE+
40xPoE+
$2,799.99
M4250-40G8XF-PoE++
40xPoE++
$4,689.99
NETGEAR AV M4250
Designed for small to mid-sized professional audio and video installations
1G / 2.5G / 10G uplinks
Reversible mount option with LEDs on the front
Silent desktop versions
NETGEAR AV M4350
Designed for large professional audio and video installations
1G / 2.5G / 10G / 25G / 100G uplinks
Redundant PSUs
Active-active core (NSF stack)
SMPTE 2110 supported on select models
Ideal to power WiFI 7 Access Points that require PoE++ and support 10G/Multi-Gig speeds
Top 5 Reasons Videoguys Recommends Netgear ProAV M4250 Switches
Engineered for AV over IP
Netgear is committed to ProAV
Easy to Configure (GUI)
Presets for NDI HX3 & NDI 6
Recommended by all our partners
Bonus! – It’s our #1 tech support solution for NDI installations
ENGAGE 2.0
Now Released!!!
Now controls AV and WiFi
New software update adds internet and wireless capabilities to AV networks
Freedom for AV & Lighting Crews
Unified Wired and Wireless Management
LAN and WLAN under Control
Auto Discovery and Onboarding Capabilities
Zero Configuration Setup
Fast Roaming and Auto-Mesh Support
NETGEAR Academy & Level 1 Certification
The OSI Model
Defining a Network
Network Topology
Unicast, Broadcast, and Multicast
Understanding Vlans
Network Termonology Overview
Learn networking concepts like Link Aggregation, STP, MLAG, and non-blocking designs
Enterprise Switch Series
Engage Controller
Specifying NETGEAR Switches
Learn more about NETGEAR below:
#5G#amp#audio#Business#Cameras#certification#classes#comprehensive#conference#course#data#Design#desktop#easy#enterprise#factor#form#Full#gui#Hardware#how#how to#insights#Internet#IP#it#lan#latency#Learn#LED
0 notes
Text
Genuine Mercedes-Benz Retrofit AMG Steering Wheel Buttons (Code U88)
Overview
The Genuine Mercedes-Benz Retrofit AMG Steering Wheel Buttons (Code U88) are advanced control accessories designed to elevate the driving experience in select AMG and Mercedes-Benz models. These buttons integrate directly into AMG performance steering wheels, providing intuitive access to dynamic driving functions. Inspired by Formula 1 design, these buttons enable a focused, ergonomic, and performance-oriented driving experience while enhancing the vehicle's sporty aesthetics.
---
Key Features
1. Genuine Mercedes-Benz Parts:
Manufactured to meet the highest standards of quality, reliability, and durability.
Specifically engineered to complement AMG performance steering wheels seamlessly.
2. Robust and Durable:
Designed for longevity, withstanding regular use and challenging driving conditions.
3. Performance-Driven Design:
The buttons are positioned ergonomically, ensuring the driver's hands remain on the wheel and eyes stay on the road.
Offers a sporty race car-like ambiance in the cockpit.
4. Customizable Functionalities:
Freely assignable functions through a combination of toggle switches and rotary controls.
5. Modern Mini-Displays:
Integrated mini screens display AMG-specific functions, such as driving mode, suspension settings, and exhaust control.
6. Enhanced Driving Control:
Simplifies quick adjustments to critical driving settings, including:
Driving Modes: Selection and display of current modes (e.g., Sport, Comfort, Race).
Manual Gear Mode: Instant activation.
AMG RIDE CONTROL Suspension: Fine-tune for dynamic handling.
Electronic Stability Program (ESP®): Activate/deactivate as needed.
AMG Performance Exhaust: Adjust exhaust sound (optional).
---
Specifications
Brand: Mercedes-Benz (AMG Division)
SKU: OSI-AMG-U88
Material: Automotive-grade components for durability and performance.
Compatibility: Retrofit for various AMG and non-AMG Mercedes-Benz models.
Installation: Professional installation required (coding and calibration recommended).
Package Contents:
1 set of AMG Steering Wheel Buttons
Retrofit accessory kit
---
Vehicle Compatibility
C-Class
W206 4-door sedan (2021 onward)
W206 C43 4-door sedan (2021 onward)
W206 C63/C63S 4-door sedan (2021 onward)
E-Class
W213 4-door saloon (2017–2020)
W213 E63/E63S AMG 4-door sedan (2016–2020)
A238 2-door cabriolet (2017–2020)
C238 2-door coupe (2017–2020)
W214 4-door sedan (2023 onward)
S214 5-door estate (2023 onward)
S-Class
W223 S63 4-door sedan (2021 onward)
EQE-Class
V295 4-door sedan (2022 onward)
X294 5-door SUV (2022 onward)
EQS-Class
V297 4-door sedan (2021 onward)
X296 5-door SUV (2022 onward)
AMG GT-Class
X290 4-door coupe (2019–2022)
SL-Class
R232 SL43, SL55, SL63 roadsters (2022 onward)
GLC-Class
X254 5-door SUV (2022 onward)
C254 5-door coupe (2023 onward)
---
Benefits
1. Enhanced Control:
Access dynamic driving functions instantly without distraction.
2. Improved Safety:
Keeps focus on the road while making adjustments.
3. Sporty Aesthetics:
Gives a professional racing vibe with high-tech displays and controls.
4. Customizable Experience:
Drivers can assign preferred AMG functions to specific buttons.
---
Applications
These AMG steering wheel buttons are specifically designed for a wide range of AMG and Mercedes-Benz models, including sedans, coupes, SUVs, estates, and roadsters. They provide an excellent retrofit solution for performance-oriented drivers who want to upgrade their vehicles' functionality and aesthetics.
---
Installation
Professional installation is highly recommended. The buttons may require coding and calibration to integrate seamlessly with the vehicle's electronic system.
---
Conclusion
The Mercedes-Benz AMG Retrofit Steering Wheel Buttons (Code U88) are the perfect accessory for drivers looking to enhance control and performance in their vehicles. Combining cutting-edge technology, ergonomic design, and customization options, these buttons transform your Mercedes-Benz into a true performance powerhouse while maintaining safety and style.
0 notes
Text
Efficient Dental AR Management Services | OSI
Simplify dental AR management. Enhance cash flow and grow your practice with our accounts receivables management services. https://www.outsourcestrategies.com/dental-ar-management/
0 notes
Text
i hate having to rework all my character designs.
i made franciscos current design back in February because I was having art block and i couldn’t draw any of my characters because they were too complex. And now that I look at it, I don’t really like franciscos design that much :( it feels more like an ugly demo rather than something final. it also looks super simplified in comparison to my other characters and im sick and tired of convincing myself that it’s because he’s “built different metaphysically.”
i have a general gist of what i want him to look like, but idk what to do. i still like the spiked hair and the scars, but i think ive been drawing him too skinny and less robot-like. ive been really when it comes to designing his clothes, but im building a good pinterest board rn to get inspiration. i still like the baggy jeans, but ive been seeing a lot of karakuri tamashii jeans in my feed and i think they’re perfect for him (not so perfect for me when i have to draw them, but it’s whatever. maybe i’ll design the embroidery in its own thing and warp it whenever i need to show his legs.) ive also been seeing a lot of baggy t shirts with these japanese woodblock painting-esque designs on them and they match very well with the jeans. ive also been really lazy about accessorizing him, but i bet he wouldn’t mind a couple fun necklaces and bracelets. maybe some cool statement belts as well. with the clothes maybe i could incorporate some patchwork or some fun textures to but idk glfivofjfbrk
i drafted up some cool jeans for him, but idk if they look good enough

what’s REALLY bothering me is his face. i really want to go for a tbhk feel with the eyes, but i don’t know how to fit them on his face without it looking weird. the overall shape of his face is bothering me too. and his nose. and his mouth. deadass they’ve just been little curved lines over the past 8 months and while it’s really convenient for drawing him quickly, it’s really fucking boring. i need to find a better face shape to put him in.
besides Francisco, there are some characters that i have completely down, and there are some that i haven’t even designed yet.
I haven’t drawn Osi, Hoshiakari, Raymond, Heavens, Dr. Chambers, Constantine or Lilith in months (at least in full-body, so i gotta put together some fits for them.) I’ve never drawn Benjamin, Giovanni, Marco, Paisley, Ophelia, or Chloe in any final way. And for Garien, Cathi, and Klaudiana, it’s been literal YEARS and none of their old designs are acceptable. Really the only one that has a clear, solid final design is Mr. 404, and he’s just a king penguin with a big ass robe and some jewelry. im currently working on a Hoshiakari reference, but that’s more for anatomy and mapping her freckles. If I make it digital, maybe I’ll put some clothes on her, but I’ll probably have to make another pinterest board. AND I HAVE SO MANY HARD ASS CHARACTER DESIGNS THAT I CANT EVEN USE BECAUSE NONE OF MY CHARACTERS MATCH. HOW THE FUCK HAS IT BEEN ALMOST 3 YEARS OF DEVELOPMENT AND NONE OF MY CHARACTERS EXCEPT FOR THE BIG PENGUIN MAN HAVE FINAL DESIGNS.
to be fair i do have a pretty good idea for what some of them dress like, i just gotta actually put it together…
fuck. i need help. someone help me.

0 notes
Text
Telecommunications Protocols: Open Systems Interconnection (OSI) Model
Usually, the analysis of communication protocol stacks begins, relatively reasonably, by considering the seven-layer Open System Interconnection model (seven-layer model or just OSI model or OSI), which the International Organization for Standardization ISO developed jointly with the telecommunications division of the International Telecommunication Union (ITU-T). The OSI model is still an excellent tool for learning the fundamentals of telecommunications network architecture, although it has not gained the popularity its creators hoped for.
The main feature of the OSI model is its openness. This means that an appropriate standardized set of protocols guarantees the possibility of interoperability between equipment from different manufacturers, which is vital not only for equipment and software manufacturers but also for telecom operators, service providers, and users since it dramatically simplifies the procedure for equipping networks.
The OSI model was developed in the 1970s based on experience gained in creating computer networks, mainly global ones. Therefore, its application area, strictly speaking, is packet data networks.
Interestingly enough, global data networks came earlier than local ones. This is explained by the history of the development of computers (computing machines), the first stage of which is associated with mainframes. These vast machines were costly and served many users, who were granted access only for a certain period. Long-distance communication channels were needed to organize such access. In the first stage, the role of such data transmission media was played by analog modems operating over voice-frequency channels (touch-tone) of analog transmission systems (Analog Data Transmission Systems, or ADTS), and the first data transmission protocols were modem protocols of physical levels that ITU-T has standardized in a series of Type V recommendations.
Since the touch-tone ADTS channel is very narrow, with a width of 300 to 3200 Hz, in addition to multi-position modulation methods for data transmission, additional efficient algorithms for using the frequency band were required, particularly data signal compression algorithms. The critical issue with modem data transmission over ADTS channels was the number of errors since touch-tone channels were initially designed only to transmit telephone signals. Therefore, the third group of V-series protocols contains, among other things, error correction protocols.
In terms of error correction, communication systems are divided into systems with and without retransmission of corrupted data elements. In transmission systems over electrical cables subject to external interference and containing many intermediate amplifiers or regenerators, the probability of errors in the data signals is very high. Therefore, the channels of these systems usually retransmit corrupt message fragments. Naturally, this method significantly reduces the data efficiency of channels.
The situation turned around with the transition to optical cables, which are well-protected from external interference and contain a small number of intermediate amplifiers and repeaters. This significantly reduced the number of errors, so it was possible to eliminate error correction at the physical layer and, if necessary, perform it at higher protocol levels.
The active development of local networks began with the advent of mini, micro, and, finally, personal computers (PCs). Thus, telephone networks first formed local ones, and only then, with technological progress, intercity ones; data transmission networks, on the contrary, evolved from global down to local.
The creation of the seven-layer OSI model was based on the following principles:
There should not be too many layers so that the design and implementation of the network are not overly complex. There should not be too few levels so that the functions performed by the levels do not turn out to be overly complex
The functioning of each level is transparent to other levels
The tasks performed by each level must be clearly delineated
The next level is created only when a new level of abstraction is needed
It is clear that solving such a problem successfully takes not only a lot of experience and knowledge but also a particular artistic approach.
Each layer of the OSI model interacts with three others: it provides services to an upper one, uses the services of a lower one, and accesses an equal (peer) layer of another computer system. More formally, a service architecture contains three essential elements: the Service User, the Service Provider, and the Service Access Point (SAP).
In this context, a service user is an OSI model layer receiving services from an adjacent OSI model layer. The service provider is the layer of the OSI model that provides services. Finally, SAP is an element of the OSI model through which one OSI layer can request a service from another OSI model layer. Simply put, SAP is nothing more than a service delivery protocol.
For example, the link layer of system A is a user of physical layer services, a service provider for the network layer of this system, and exchanges information with the link layer of system B.
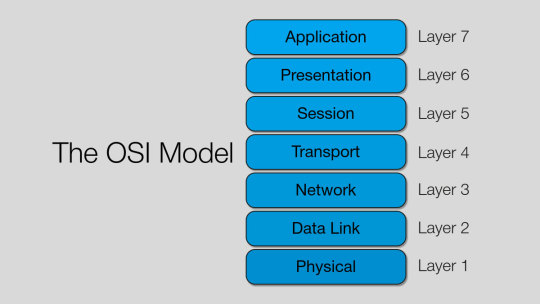
OSI Layers and Layer Groups
Each layer of the OSI model performs specific functions necessary for the system's proper functioning. Let's list the seven layers of the OSI model from top to bottom and describe their main functions.
Implementations of the four upper layers of the OSI model (application, presentation, session, and transport) can be found in every peripheral device; the three lower layers (network, data link, and physical) are present at all intermediate (transit) connection points between endpoints.
Therefore, all the OSI model layers can be divided into two functionally different groups: the upper and lower layers. The first—also called 'Host Layers' or 'end-end'—are responsible for the operation of applications and are implemented only in software products. The second—'Media Layers' or 'chained'—transmits data. Moreover, the physical and data link layers contain software and hardware components.
A common feature of the three lower levels is that they can support any type of data (including service data) generated by the four upper levels. In other words, the lower levels are utterly indifferent to the data they transmit and are solely concerned with delivering it from one point to another.
Host Layers OSI
In this part, we will talk about the four upper levels that ensure the operation of network applications.
The Application Layer provides services directly to the user's apps. It forms a set of open and standard application programming interfaces (APIs). Implementing the application layer might be complex because many applications use its services. Examples of OSI application layer protocols are distributed directory services by the ITU-T X.500 recommendation and its "lightweight" version (Lightweight Directory Access Protocol, LDAP), as well as remote procedure calls (RPC). The latter is a very efficient way to distribute computing power between the client and the server.
The Presentation Layer performs general data transformation. One of the services at this level is encryption, which ensures information security. In particular, Web server software includes encryption protocols to protect customers' financial information. Another example of a presentation-level service is compression, which reduces the amount of data sent between two computers. Thus, many virtual private network (VPN) implementations use tunneling protocols, where a packet of one protocol is placed inside another packet. The tunneling mechanism requires adding significant service information to the transmitted data, which can be easily compressed. Therefore, VPNs usually include a compression algorithm.
Another typical operation of the presentation level is transcoding, which is less complex than encrypting/decrypting or compressing/decompressing. An example of transcoding is the conversion of ASCII codes to EBCDIC and back according to specific tables. Still, such simple transcoding operations are only sometimes possible. Therefore, the International Organization for Standardization (ISO) has developed a special Abstract Syntax Notation program version 1 (ASN.1), which helps programs running on different machines and written in different programming languages to exchange data.
The Session Layer provides additional services to the transport layer if the connection session is established first. In addition to managing data back and forth, the most important functions of this layer are starting and terminating the session and syncing data. Session layer services are unused if the connection does not need to be established.
The Transport Layer performs error-free, message-oriented end-to-end transmission, and it must support this function regardless of the reliability of the underlying layer. The underlying layer is especially unreliable during packet transmission in connectionless communication. In this case, the transport layer must be 'smart' enough to compensate for the weaknesses of the underlying layer. Due to its greater reliability, the transport layer can be less complex in a connection-oriented packet network. Finally, the underlying service can be highly robust, connection-oriented with channel switching, and have a reliable link-layer protocol. In this case, the transport layer does not need to do anything to ensure consistently high transmission quality. Thus, the complexity of the transport layer is inversely proportional to the reliability of the underlying layers. To perform its main task—error-free delivery of messages—the transport layer provides the functions of addressing, opening, and closing connections, assigning priority to data, monitoring and error correction, data flow control, failure recovery, and multiplexing.
Continued in the next Around Cable category post.
0 notes
Text
what are vpn proxy settings
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what are vpn proxy settings
VPN Encryption Protocols
VPN encryption protocols are essential components of virtual private networks, ensuring the security and privacy of data transmitted over the internet. These protocols establish the rules and methods for encrypting and decrypting data, safeguarding it from unauthorized access or interception by malicious entities.
One of the most widely used VPN encryption protocols is OpenVPN. It is an open-source protocol known for its robust security features and flexibility. OpenVPN utilizes OpenSSL encryption library and supports various encryption algorithms, including AES (Advanced Encryption Standard) and Blowfish. Its open nature allows for constant scrutiny and updates by the security community, enhancing its resilience against emerging threats.
Another commonly employed protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec can be implemented in two modes: Transport mode, which encrypts only the data payload, and Tunnel mode, which encrypts the entire data packet. It offers strong security mechanisms such as authentication, integrity verification, and encryption, making it suitable for securing communications between networks.
L2TP/IPSec (Layer 2 Tunneling Protocol with IPSec) combines the best aspects of L2TP and IPSec protocols. L2TP provides the tunneling mechanism, while IPSec offers encryption and authentication capabilities. Although it may not be as fast as other protocols due to double encapsulation, L2TP/IPSec is highly secure and widely supported across various platforms.
In recent years, WireGuard has gained attention for its simplicity and efficiency. It aims to be leaner and faster than traditional VPN protocols while maintaining robust security. WireGuard utilizes state-of-the-art cryptographic techniques, such as the Noise protocol framework, to ensure secure communication channels.
Choosing the right VPN encryption protocol depends on factors such as security requirements, performance, and compatibility with devices and platforms. By understanding the strengths and weaknesses of each protocol, users can make informed decisions to safeguard their online activities and data privacy.
Proxy Server Configuration
Title: Configuring Proxy Servers: A Comprehensive Guide
Proxy servers serve as intermediaries between a user's device and the internet. They enhance security, privacy, and performance by acting as a buffer between the user and the web resources they access. Configuring proxy servers is essential for organizations and individuals seeking to optimize their internet usage. Here's a comprehensive guide on proxy server configuration.
Choose the Right Proxy Type:
There are various types of proxies, including HTTP, HTTPS, SOCKS, and transparent proxies. Understand your requirements to select the most suitable type.
Obtain Proxy Server Details:
Before configuration, gather essential information such as the proxy server's IP address, port number, and authentication credentials if required.
Configuration Methods:
Manual Configuration: Users can configure proxies manually in their device or application settings by entering the proxy details.
Proxy Auto-Configuration (PAC): PAC files automate proxy configuration based on predefined rules, simplifying management for large networks.
Network Settings Configuration:
In Windows, navigate to Control Panel > Network and Internet > Internet Options to configure proxy settings.
On macOS, proxy settings can be adjusted in System Preferences > Network > Advanced.
Linux users can configure proxies through network configuration files or using command-line tools like 'export http_proxy' for temporary settings.
Testing and Troubleshooting:
After configuration, test the proxy connection to ensure it functions as expected.
Common issues include incorrect proxy details, network restrictions, or firewall blocks. Troubleshoot by verifying settings and checking network connectivity.
Proxy Server Maintenance:
Regularly review and update proxy configurations to adapt to changing network requirements.
Monitor proxy server performance and security to address any issues promptly.
Configuring proxy servers enhances internet security, privacy, and efficiency. By following this guide, users can set up and maintain proxy servers effectively to suit their needs.
VPN Tunneling Methods
Title: Exploring VPN Tunneling Methods: Ensuring Secure Online Communication
Virtual Private Networks (VPNs) have become indispensable tools for safeguarding online privacy and security. At the heart of their functionality lies the concept of tunneling, a process that encapsulates data within a secure "tunnel" for transmission over the internet. Understanding VPN tunneling methods is crucial for comprehending how these networks protect sensitive information from prying eyes.
There are several VPN tunneling protocols, each offering unique features and levels of security. One commonly used protocol is OpenVPN, known for its open-source nature and robust encryption capabilities. OpenVPN employs SSL/TLS protocols to create secure connections, making it a preferred choice for many users and businesses alike.
Another widely used protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec can be configured in two modes: Transport mode, which encrypts only the data payload, and Tunnel mode, which encrypts both the data payload and the original IP header. This versatility makes IPSec suitable for various network architectures.
L2TP/IPsec (Layer 2 Tunneling Protocol with IPsec) combines the best aspects of both L2TP and IPSec. L2TP provides the tunneling mechanism, while IPsec ensures data confidentiality and integrity. While L2TP/IPsec offers strong security, it may not be as fast as other protocols due to its double encapsulation process.
SSTP (Secure Socket Tunneling Protocol) is another VPN tunneling method developed by Microsoft. It establishes a secure connection over the SSL/TLS channel, making it highly resistant to censorship and firewall restrictions. SSTP is particularly useful for users in regions with stringent internet regulations.
Lastly, WireGuard has gained attention for its simplicity and efficiency. This modern VPN protocol aims to offer better performance and security than traditional protocols while maintaining a minimalistic design.
In conclusion, VPN tunneling methods play a vital role in ensuring secure and private communication over the internet. By understanding the strengths and weaknesses of each protocol, users can make informed decisions to protect their online activities effectively.
Proxy Authentication Settings
Proxy authentication settings are vital components of secure internet browsing, particularly in corporate or organizational networks. These settings allow users to authenticate themselves before accessing the internet through a proxy server, adding an extra layer of security and control.
Proxy servers act as intermediaries between a user's device and the internet. They can enhance security by filtering web content, improving performance by caching frequently accessed resources, and providing anonymity by masking the user's IP address. However, to access the internet through a proxy server, users often need to authenticate themselves, ensuring that only authorized individuals can utilize the network resources.
There are several methods of proxy authentication, including basic authentication, which requires users to enter a username and password, and NTLM (Windows NT LAN Manager) authentication, which uses a challenge-response mechanism for validation. Additionally, some proxy servers support more advanced authentication methods like Kerberos or OAuth, offering enhanced security features.
Configuring proxy authentication settings typically involves accessing the network settings of the device or web browser and entering the required authentication details provided by the network administrator. It's essential for users to choose strong, unique passwords to prevent unauthorized access to the proxy server and safeguard sensitive information.
Proxy authentication settings are particularly crucial for businesses and organizations that need to enforce access controls and monitor internet usage to maintain regulatory compliance and protect against security threats. By implementing robust proxy authentication mechanisms, organizations can ensure that only authorized users can access the internet through their networks, reducing the risk of unauthorized access and data breaches.
VPN Proxy Compatibility
VPN Proxy Compatibility: Ensuring Seamless Online Security and Access
VPN proxies serve as indispensable tools in safeguarding online privacy and accessing geo-restricted content. However, ensuring compatibility between VPNs and proxies is crucial for maximizing their effectiveness and avoiding potential pitfalls.
Firstly, it's essential to understand the distinction between VPNs and proxies. VPNs encrypt users' internet traffic and route it through remote servers, enhancing privacy and security. On the other hand, proxies act as intermediaries between users and the internet, masking their IP addresses and allowing access to geo-blocked content.
When it comes to compatibility, VPNs and proxies can complement each other effectively. Users can employ proxies alongside VPNs to enhance anonymity and bypass geo-restrictions simultaneously. However, ensuring compatibility requires careful configuration and selection.
One key consideration is protocol compatibility. VPNs typically support various protocols like OpenVPN, L2TP/IPsec, and IKEv2, each with its strengths and weaknesses. Similarly, proxies utilize different protocols such as HTTP, HTTPS, SOCKS4, and SOCKS5. Ensuring that the VPN and proxy protocols align can prevent connectivity issues and ensure seamless browsing.
Furthermore, users must verify that their chosen VPN provider supports proxy usage. Some VPNs may restrict or discourage the use of proxies, citing security concerns or compatibility issues. Researching VPN providers' policies and capabilities is essential to avoid conflicts and ensure a smooth user experience.
Additionally, users should assess the compatibility of VPN and proxy configurations with their intended use cases. Certain activities, such as torrenting or accessing streaming services, may require specific configurations to bypass restrictions effectively.
In conclusion, VPN proxy compatibility is crucial for maximizing online security and access. By understanding the nuances of both technologies and ensuring proper configuration, users can enjoy a seamless and secure browsing experience.
0 notes
Text
does a vpn help with wireshark
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn help with wireshark
VPN encryption
Title: Understanding VPN Encryption: Securing Your Online Privacy
In today's digital age, where cyber threats lurk around every corner of the internet, safeguarding your online privacy has become paramount. Virtual Private Networks (VPNs) have emerged as a crucial tool in this endeavor, offering users a secure and private connection to the internet. At the heart of every VPN lies encryption – a complex process that ensures the confidentiality and integrity of data transmitted over the network.
VPN encryption works by encoding data into an unreadable format, making it indecipherable to anyone who intercepts it without the encryption key. This process effectively creates a secure "tunnel" through which your data travels, protecting it from prying eyes, hackers, and other malicious entities.
There are several encryption protocols used by VPN providers, each offering varying levels of security and performance. Some of the most common encryption protocols include:
AES (Advanced Encryption Standard): Widely regarded as one of the most secure encryption algorithms, AES employs symmetric-key cryptography to encrypt and decrypt data. It comes in different key lengths, with AES-256 being the strongest and most commonly used variant.
OpenVPN: This open-source protocol combines both security and flexibility, making it a popular choice among VPN users. OpenVPN uses SSL/TLS protocols for key exchange and authentication and can be configured to use various encryption algorithms, including AES.
IPsec (Internet Protocol Security): IPsec operates at the network layer of the OSI model and provides end-to-end security through encryption and authentication protocols. It is often used in combination with other encryption algorithms like AES for enhanced security.
WireGuard: A relatively new addition to the VPN encryption landscape, WireGuard aims to offer better performance and security compared to traditional protocols like OpenVPN and IPsec. It utilizes state-of-the-art cryptographic techniques to ensure fast and secure connections.
In conclusion, VPN encryption is a critical component of online security, providing users with the means to protect their sensitive data and maintain their privacy in an increasingly interconnected world. By understanding how encryption works and choosing a VPN provider that prioritizes security, individuals can enjoy a safer and more secure browsing experience.
Wireshark analysis
Title: Unlocking Insights: A Beginner's Guide to Wireshark Analysis
In the realm of network troubleshooting and cybersecurity, Wireshark stands as a powerful tool, offering deep insights into network traffic and packet-level analysis. Whether you're a seasoned network administrator or a curious enthusiast, mastering Wireshark can enhance your understanding of network protocols and aid in diagnosing various network issues.
Wireshark, an open-source packet analyzer, allows users to capture and interactively browse the traffic running on a computer network. Its versatility enables it to work across different operating systems, making it a popular choice among professionals and hobbyists alike.
The process of Wireshark analysis involves capturing packets transmitted over a network, which can include data such as emails, passwords, and website visits. By examining these packets, users can identify potential security threats, performance bottlenecks, and protocol errors.
Getting started with Wireshark analysis requires installing the software and setting up packet capture filters to focus on specific types of traffic. Once the packets are captured, users can utilize Wireshark's extensive set of features to analyze the data, including packet filtering, packet decoding, and protocol analysis.
Wireshark's user-friendly interface simplifies the process of analyzing packets, allowing users to visualize network traffic in real-time and drill down into individual packets for detailed inspection. Additionally, Wireshark supports various protocols, including Ethernet, Wi-Fi, TCP/IP, and HTTP, making it a versatile tool for analyzing different types of network traffic.
In conclusion, Wireshark analysis is a valuable skill for anyone working in the field of networking or cybersecurity. By leveraging its capabilities, users can gain valuable insights into network behavior, troubleshoot issues effectively, and strengthen the security posture of their systems. Whether you're a novice or an expert, mastering Wireshark can unlock a wealth of knowledge about network communication.
Network privacy
In the digital age, network privacy has become an increasingly important concern for individuals and organizations alike. Network privacy refers to the protection of sensitive information and data shared over a network from unauthorized access or disclosure. With the rise of cyber threats and data breaches, ensuring network privacy has become essential to safeguard personal and confidential information.
One of the key aspects of network privacy is encryption. Encryption helps to secure data by converting it into a code that can only be deciphered with the appropriate decryption key. This technology is widely used to protect sensitive information such as passwords, financial transactions, and communication between users on a network.
Virtual Private Networks (VPNs) are another valuable tool for enhancing network privacy. A VPN creates a secure and encrypted connection over a public network, such as the internet, shielding users' online activities from prying eyes. By routing internet traffic through a VPN server, users can browse the web anonymously and prevent their online activities from being tracked.
Implementing strong authentication measures, such as multi-factor authentication, is crucial for strengthening network privacy. This additional layer of security helps to verify the identity of users accessing a network, reducing the risk of unauthorized access and data breaches.
Overall, prioritizing network privacy is essential in safeguarding sensitive information in an increasingly connected world. By utilizing encryption, VPNs, and robust authentication measures, individuals and organizations can better protect their data and mitigate the risks associated with cyber threats.
Data packet monitoring
Data packet monitoring is a crucial aspect of network management and cybersecurity. It involves the systematic observation and analysis of data packets as they traverse a network. These packets contain information such as source and destination addresses, data payload, and protocol type. By monitoring these packets, network administrators can gain valuable insights into network traffic, detect anomalies, and troubleshoot issues.
One of the primary purposes of data packet monitoring is to ensure network security. By inspecting packet headers and payloads, administrators can identify suspicious activities such as unauthorized access attempts, malware infections, and data exfiltration. This proactive approach allows organizations to respond swiftly to potential threats and mitigate risks before they escalate.
Furthermore, data packet monitoring plays a vital role in network performance optimization. By analyzing packet flow and latency, administrators can identify bottlenecks and optimize network configurations to improve efficiency and responsiveness. This enables organizations to deliver better user experiences and maximize the productivity of their network infrastructure.
In addition to security and performance benefits, data packet monitoring also facilitates compliance with regulatory requirements. Many industries, such as healthcare and finance, are subject to strict data protection regulations that require monitoring and auditing of network traffic. By implementing comprehensive packet monitoring solutions, organizations can ensure compliance with these regulations and avoid costly penalties.
Overall, data packet monitoring is an essential practice for any organization that relies on network connectivity. By providing insights into network activity, enhancing security, optimizing performance, and facilitating compliance, packet monitoring enables organizations to maintain a secure, efficient, and compliant network infrastructure.
Online security measures
Online security measures are crucial in today's digital landscape, where cyber threats abound. Whether you're browsing the web, conducting financial transactions, or communicating online, implementing effective security measures is essential to protect your data and privacy. Here are some key measures individuals and businesses can take to enhance online security:
Strong Passwords: Use complex passwords with a mix of letters, numbers, and special characters. Avoid using easily guessable information like your name or birthdate.
Two-Factor Authentication (2FA): Enable 2FA whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
Secure Connections: Ensure that websites you visit use HTTPS encryption, especially when providing sensitive information like login credentials or payment details. Avoid connecting to public Wi-Fi networks for sensitive activities.
Regular Software Updates: Keep your operating system, antivirus software, web browsers, and other applications up to date with the latest security patches. Many cyber attacks exploit vulnerabilities in outdated software.
Firewalls and Antivirus Software: Install reputable antivirus software and enable firewalls on your devices to block malicious traffic and prevent unauthorized access.
Data Encryption: Use encryption tools to protect sensitive data, both in transit and at rest. Encryption scrambles information so that it's unreadable without the decryption key.
Awareness and Education: Stay informed about common online threats such as phishing scams, malware, and social engineering attacks. Educate yourself and your team on how to recognize and avoid these threats.
Backup Regularly: Regularly backup your important files and data to an external hard drive or cloud storage service. In the event of a security breach or data loss, you'll have a copy of your information.
By implementing these online security measures, you can minimize the risk of falling victim to cyber attacks and safeguard your digital presence. Remember that maintaining vigilance and staying proactive are key components of a robust cybersecurity strategy.
0 notes
Text
Exploring Layer 3 Managed Network Switches with the GWN7802P
The fast-paced world of networking solutions, Layer 3 managed network switches have become indispensable for businesses striving for efficient and scalable network architecture. Among the myriad of options available, the GWN7802P stands out as a reliable and feature-rich choice. This article delves into the essential aspects of Layer 3 managed network switches and highlights the unique capabilities of the GWN7802P.
Understanding Layer 3 Managed Network Switches: Layer 3 managed network switches play a crucial role in optimizing network performance by operating at the network layer of the OSI model. Unlike their Layer 2 counterparts, these switches possess the intelligence to route data based on IP addresses, resulting in more streamlined and efficient data transmission. This capability becomes especially valuable in large-scale networks where routing and subnets are essential for seamless communication.
Introducing the GWN7802P: The GWN7802P emerges as a standout performer in the realm of Layer 3 managed network switches. With a host of advanced features, this switch is purpose-built to meet the demands of contemporary businesses. Boasting Power over Ethernet (PoE) support, the GWN7802P eliminates the need for separate power sources for connected devices, simplifying cable management and reducing overall costs.
One of the notable features of the GWN7802P is its robust security infrastructure. The switch incorporates advanced security protocols, including VLAN support, Access Control Lists (ACLs), and port security, ensuring a secure and protected network environment. Businesses can trust that their sensitive data is shielded from unauthorized access.
Scalability is another key advantage offered by the GWN7802P. With a high port density and the ability to stack multiple switches, this solution is tailored to accommodate the growing needs of expanding networks. The switch's user-friendly management interface further enhances ease of use, allowing network administrators to configure and monitor the network effortlessly.
Conclusion:
The GWN7802P epitomizes the evolution of Layer 3 managed network switches, providing a comprehensive solution for businesses seeking top-tier performance, security, and scalability. With its advanced features and resilient design, the GWN7802P is a dependable choice for organizations navigating the complexities of modern networking. Investing in Layer 3 managed network switches, particularly the GWN7802P, is a strategic step toward building a robust and future-ready network infrastructure capable of supporting the evolving needs of today's dynamic business landscape. Embrace the power of Layer 3 networking with the GWN7802P to unlock new possibilities for your business.
0 notes
Text
Exploring Load Balancing in AWS: A Comprehensive Guide
In today’s digital landscape, ensuring high availability, scalability, and performance of applications is crucial. One of the key components that enable these capabilities in the cloud is load balancing.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

Elastic Load Balancer (ELB): The Elastic Load Balancer (ELB) service provided by AWS is a powerful tool for distributing incoming network traffic across multiple resources.
ELB supports three types of load balancers, each catering to specific use cases:
Classic Load Balancer (CLB): The Classic Load Balancer operates at the transport layer (Layer 4) of the OSI model. It is an ideal choice for applications that require simple load balancing across multiple EC2 instances.
Application Load Balancer (ALB): The Application Load Balancer operates at the application layer (Layer 7) and offers advanced features. ALB supports content-based routing, path-based routing, and integrates well with microservices architectures.
Network Load Balancer (NLB): The Network Load Balancer is designed for handling high volumes of traffic with ultra-low latency. It operates at the transport layer (Layer 4) and is capable of handling TCP, UDP, and TLS traffic efficiently.
If you want to learn more about AWS Certification Online, you contact best institute because they offer certifications and job placement opportunities. Experienced teachers can help you learn better. You can find these services both online and offline. Take things step by step and consider enrolling in a course if you’re interested.

3. SSL/TLS Termination: Handling SSL/TLS encryption and decryption can be resource-intensive for backend servers. AWS load balancers offer SSL/TLS termination functionality, offloading this computational burden from your resources. With SSL/TLS termination, load balancers can handle the encryption and decryption processes, enhancing performance and simplifying SSL/TLS certificate management.
4. Cross-Zone Load Balancing: By default, AWS load balancers distribute traffic evenly across all registered resources in different Availability Zones. However, with Cross-Zone Load Balancing, each Availability Zone receives an equal distribution of traffic, regardless of the number of resources in each zone. This ensures optimal utilization of your infrastructure across multiple zones.
5. Sticky Sessions: Some applications require maintaining session state for users. AWS load balancers support sticky sessions, also known as session affinity. Sticky sessions route requests from a particular client consistently to the same backend resource, preserving session state. This is particularly useful for stateful applications and can enhance performance and user experience.
Load balancing is a critical aspect of building scalable and highly available applications in AWS. With the Elastic Load Balancer (ELB) service, AWS provides a range of load balancing options to suit different application requirements.
Whether you need basic load balancing, advanced routing capabilities, or high-performance handling of heavy traffic loads, AWS load balancers have got you covered. By leveraging these load balancing services, you can optimize your application infrastructure, improve reliability, and deliver a seamless user experience.
Remember, load balancing is not a one-size-fits-all solution. It’s important to evaluate your application’s specific needs and choose the appropriate load balancer type to achieve the desired outcomes.
0 notes
Text
Allen OSI Jackson table C-arm O-arm Spine operating table
Allen OSI Jackson table C-arm O-arm Spine operating table
Our latest modular table platform, offering enhanced safety features, improved setup workflows, and increased weight capacity.Enhanced patient positioning for spine, imaging and orthopedic trauma This modern system features a dual column modular platform known for its interchangeable patient positioning for spine, imaging, and orthopedic trauma procedures. It features a unique tabletop mounting interface that keeps the tabletop locked in place, single push electronic floor locks and a streamlined 180° patient rotation mechanism. Simple to set up and intuitive to use, it simplifies your workflow and minimizes the possibility of human error.
Product features *Tower and ratchet system that provides a unique tabletop mounting interface resulting in secure connection and adjustable table top height before and after patient transfer
*Carbon fiber construction for complete radiolucency, allowing unrestricted C-arm and O-arm access *Streamlined 180° patient rotation mechanism *Customizable pad and component placement to meet individual patient needs
Whatsapp+8615146602893
email:[email protected]
Allen OSI Jackson table C-arm O-arm Spine operating table
Spinal Surgery Top Open spine frame reduces vena cava compression, minimizes epidural venous bleeding and improves visualization at the surgical site Radiolucent Imaging Top Supports supine or lateral positions Fully radiolucent, carbon fiber table top with pressure equalization pad Orthopedic Trauma Top Modern table top with Traction Arc attachment features Traction Arc provides constant and anatomically correct traction for various trauma procedures Secure and flexible with multiple component options for either skin or skeletal traction Enhanced radiolucency by design.
Whatsapp+8615146602893
email:[email protected]











0 notes
Text
Configuring Port Address Translation (PAT) In Cisco Packet Tracer: A Guide To Efficient Network Address Translation
Introduction
Port Address Translation (PAT), also known as NAT Overload, is a powerful network address translation technique used to conserve public IP addresses and enable multiple devices on a private network to share a single public IP address. Cisco Packet Tracer, a versatile network simulation tool, provides an excellent platform to understand and practice PAT configurations in a controlled environment. In this comprehensive blog post, we will explore the significance of PAT in modern networking, learn how to configure pat configuration in packet tracer, and understand the benefits of this technique in optimizing network resources.

Section 1: Understanding Port Address Translation
Network Address Translation (NAT) is essential for translating private IP addresses used within a local network into public IP addresses used on the internet. PAT is a form of NAT that operates at the transport layer (Layer 4 of the OSI model), allowing multiple private IP addresses to be mapped to a single public IP address. PAT uses unique port numbers to distinguish between different connections and ensure the correct routing of traffic to the appropriate devices.
Section 2: Configuring PAT on Cisco Routers in Packet Tracer (approx. 250 words)
Step 1: Access the Router CLI In Packet Tracer, access the router's Command Line Interface (CLI) to begin configuring PAT.
Step 2: Configure the Inside and Outside Interfaces Designate the interfaces connected to the private and public networks using the "interface" command. For example:
scssCopy code
Router(config)# interface FastEthernet0/0 Router(config-if)# ip address 192.168.1.1 255.255.255.0 Router(config)# interface FastEthernet0/1 Router(config-if)# ip address [Public IP] [Subnet Mask]
Step 3: Enable NAT Overload (PAT) To enable PAT, use the "ip nat inside" command on the inside interface and the "ip nat outside" command on the outside interface. Then, apply the overload keyword to enable PAT. For example:
scssCopy code
Router(config)# ip nat inside source list 1 interface FastEthernet0/1 overload
Step 4: Create an Access Control List (ACL) Create an ACL to specify which private IP addresses should be translated using PAT. For example:
arduinoCopy code
Router(config)# access-list 1 permit 192.168.1.0 0.0.0.255
Section 3: Benefits of PAT in Network Address Translation
Address Conservation: PAT allows multiple devices on a private network to share a single public IP address, optimizing the use of scarce public IP resources.
Enhanced Security: By hiding private IP addresses behind a single public IP, PAT adds an additional layer of security to the network, reducing the exposure of internal devices to potential threats.
Simplified Network Management: PAT reduces the complexity of managing public IP addresses and minimizes the need for manual IP address assignments.
Seamless Internet Connectivity: PAT facilitates transparent internet access for all devices on the private network, providing a smooth and efficient online experience for users.
Section 4: Practical Implementation of PAT in Packet Tracer
Using Packet Tracer, simulate a network scenario with a private network and a router connecting to the internet. Configure PAT on the router to enable internet access for devices on the private network. Test connectivity from multiple devices to the internet and observe how PAT translates private IP addresses to the single public IP address.
Section 5: Troubleshooting PAT in Packet Tracer
Common issues when configuring PAT in Packet Tracer include misconfigured access control lists (ACLs) or missing "ip nat inside" and "ip nat outside" commands on the respective interfaces. Troubleshoot these issues by verifying the ACL configuration and ensuring that the inside and outside interfaces are correctly designated.
Section 6: Conclusion
Port Address Translation (PAT) is a crucial NAT technique that conserves public IP addresses and enhances network security and management. In Cisco Packet Tracer, network enthusiasts, students, and professionals can practice PAT configurations to gain valuable hands-on experience with this essential networking technology. By implementing PAT, organizations can optimize their network resources, secure internal devices, and ensure seamless internet connectivity for all users. Embrace PAT in Packet Tracer to elevate your networking skills and build a more efficient and secure network infrastructure.
0 notes
Text
mermay vibes w my main (i think?) oc !! although technically mermaids/mermen are supposed to have fish tails and mantis shrimps are crustaceans bUt what's the difference other than an exoskeleton really ;D

#mermay#mantis shrimps are so incredibly cool#oc lore in case someone wants to know something abt this story:#he's a TGO (transgenic organism) with mantis shrimp genes transferred into his dna :)))#i mean#if you simplify it enough#osi's ocs !!#project051_#mermaid#merman#that's such a dumb term btw#oc
14 notes
·
View notes